What is an Information Security Policy? Why is it Necessary?
by Danny Tehrani | Jan 09, 2025

According to CloudSecureTech, worldwide spending on data security has reached $81.6 billion. This is an alarming statistic that underscores the reality many businesses face today. Without a robust information security policy, your business is vulnerable to financial losses, reputation damage, and operational disruptions.
“Think of an information security policy as your business’s digital seatbelt—essential for navigating today’s online terrain,” says Danny Tehrani, CEO at Computers Made Easy.
But what exactly does this policy mean for your business, and how can you create one effectively? This guide will explain the concept, its significance, and actionable steps to implement it seamlessly. Let’s dive in.
Ready to Safeguard Your Business from Cyber Threats?
Take the first step towards comprehensive security!
Learn MoreWhat Is an Information Security Policy and Why Does It Matter?
An information security policy is the backbone of your business’s digital defense strategy. It establishes a structured framework to safeguard sensitive data and IT infrastructure from cyber threats. This includes defining access controls, outlining user responsibilities, and specifying responses to potential breaches.
Clear standards and protocols ensure consistent practices across your organization, aligning technical measures with business goals to minimize risks effectively.
Why You Need an Information Security Policy Now
- Compliance Requirements: Many regulatory bodies, such as HIPAA, require businesses to implement clear security protocols.
These mandates are designed to ensure the confidentiality, integrity, and availability of sensitive data. Non-compliance can result in hefty fines, legal consequences, and reputational damage, making adherence not just a legal necessity but a cornerstone of responsible business operations.
- Mitigates Cyber Risks: A comprehensive information security policy fortifies your business against diverse cyber threats, including ransomware, phishing, and malware.
By implementing proactive measures such as regular employee training, advanced threat detection systems, and data encryption, you significantly reduce the likelihood of breaches. These protocols not only shield your operations but also ensure swift recovery and continuity in case of an attack.
- Fosters Customer Trust: By implementing a robust information security policy, you demonstrate a commitment to safeguarding your clients’ data, ensuring their sensitive information remains protected and establishing your business as a reliable and trustworthy partner in the digital market.
More articles you might like: |
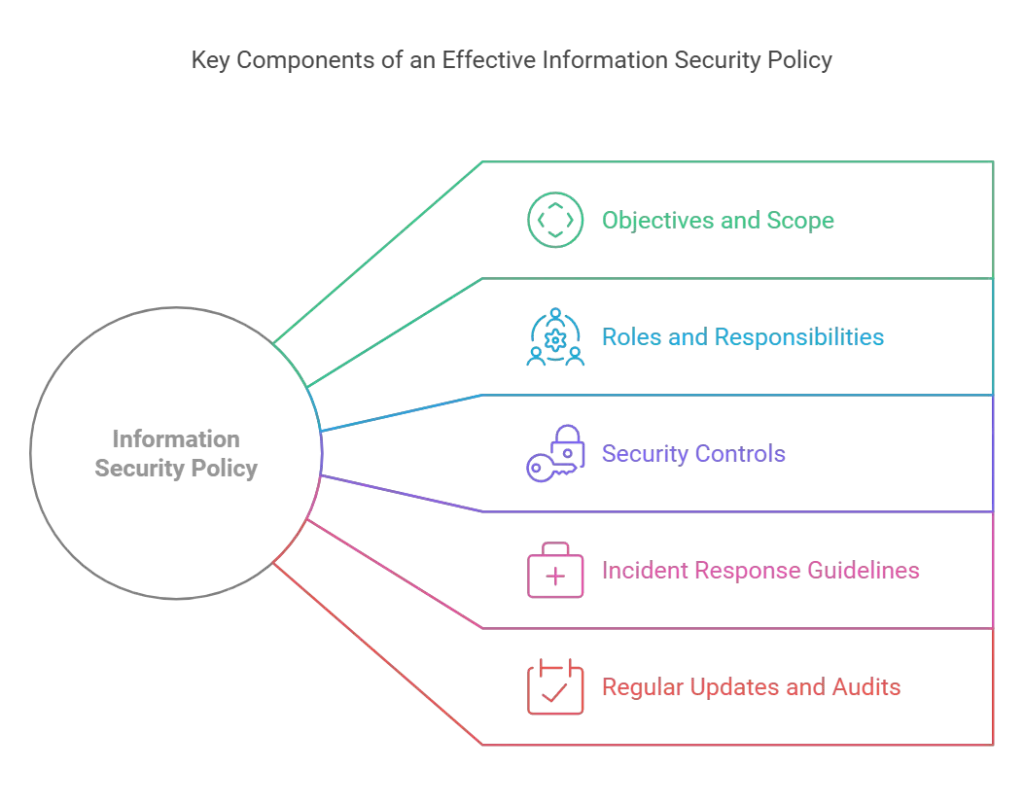
Building Blocks of a Strong Information Security Policy
Creating an effective policy doesn’t have to be overwhelming. Here are the essential components:
1. Define Objectives and Scope
Begin by identifying what your information security policy should achieve. For instance:
- Scope: Identify systems, data types, and personnel it covers.
- Goals: Establish measurable security outcomes like reducing incidents by 20% annually.
2. Outline Roles and Responsibilities
Who’s in charge of your security framework? Ensure accountability with clear assignments for:
- IT teams managing technical safeguards.
- Employees adhering to usage policies.
- Executives supporting compliance initiatives.
3. Detail Security Controls
Address the core areas:
- Physical Security: Restricted server room access.
- Data Encryption: Encrypt sensitive data in transit and at rest.
- Access Management: Enforce multi-factor authentication for system logins.
4. Include Incident Response Guidelines
Your information security policy template must outline:
- How to detect, report, and mitigate breaches.
- Clear timelines for restoring affected systems.
- Communication plans for informing stakeholders.
5. Regularly Update and Audit Your Policy
An outdated policy is ineffective. Conduct annual reviews to:
- Align with emerging threats.
- Meet new compliance standards.
- Gather feedback for improvement.
Crafting Policies for Small Businesses: Simplified Steps
Using an information security policy template for small businesses can streamline your process. Here’s how:
- Start Small: Begin with templates tailored to businesses your size.
- Focus on Essentials: Highlight critical areas like endpoint protection and secure Wi-Fi access.
- Get Expert Help: Consider outsourcing policy creation to experienced providers like CME Services.
Need Inspiration? Here Are Comprehensive Examples of Information Security Policies
A strong information security policy framework includes detailed and targeted policies that address various facets of cybersecurity. Below are examples of critical policies every business should consider implementing to ensure a robust security posture:
- Acceptable Use Policy: Clearly defines permissible and prohibited activities on company devices and networks, ensuring employees adhere to safe practices.
- Data Retention Policy: Specifies how long data should be stored, the conditions for archiving, and protocols for secure deletion to comply with legal and business requirements.
- BYOD (Bring Your Own Device) Policy: Establishes guidelines for using personal devices at work, including security software requirements and acceptable data usage.
- Password Management Policy: Enforces the use of strong, regularly updated passwords and multi-factor authentication to secure system access.
- Incident Response Plan: Outlines step-by-step actions to detect, report, and resolve security incidents efficiently.
- Third-Party Vendor Management Policy: Details how to evaluate and monitor external partners to ensure their practices align with your security standards.
- Remote Work Security Policy: Provides guidelines for securing home networks, using VPNs, and maintaining confidentiality while working remotely.
These examples serve as foundational pillars for businesses of all sizes to mitigate risks and foster a culture of security awareness. Also, reviewing samples of information security policies can provide valuable insights and shortcuts when drafting your own.
Quick Comparison: Custom vs. Template Policies
| Aspect | Custom Policy | Template Policy |
| Cost | Higher upfront cost | Cost-effective |
| Time to Implement | Several weeks | Immediate |
| Customization | Tailored to your specific needs | Requires manual adjustments |
| Scalability | Easily scalable as business grows | Limited without significant edits |
Act Now to Protect Your Business with CME Services
A well-crafted information security policy is your business’s first line of defense against evolving cyber threats. It safeguards sensitive data, ensures compliance with industry standards, and builds trust among your clients.
Ready to strengthen your organization’s cybersecurity posture? Computers Made Easy (CME Services) offers expert guidance and tailored solutions to help you design and implement a robust security framework.
Don’t wait for a breach to occur—contact us today to schedule your consultation and secure your business’s future!



