The Top 10 Most Dangerous Cloud Malware Attacks Threatening Your Business
by Danny Tehrani | Feb 25, 2025

According to SonicWall’s 2022 Cyber Threat Report, there were over 2.8 billion malware attacks in the first half of 2022 alone, an increase of 11% over the previous 12 months .
“As more businesses shift to the cloud, attackers continually evolve their tactics to exploit new vulnerabilities.” – Danny Tehrani, CEO of Computers Made Easy.
You face escalating risks from malicious actors who see your cloud environment as a goldmine. And the costs aren’t just about money—downtime, lost trust, and compliance violations could knock you back hard. Ever wonder which threats are the worst offenders? Below, you’ll find ten attacks that can cripple your operations if left unchecked. Let’s dig into each threat and explore how you can stay one step ahead.
What Exactly Is Cloud Malware?
Cloud malware is malicious software designed to infiltrate and exploit data, applications, or services hosted in the cloud. While traditional malware targets on-premises servers and individual machines, cloud malware focuses on accessing offsite data centers or hijacking cloud-based applications.
Attackers take advantage of shared resources, potentially affecting multiple tenants on the same cloud platform. Because cloud environments often allow rapid scaling and remote access, cybercriminals can quickly spread malware or leverage vulnerabilities across entire infrastructures. This makes robust, cloud-specific security measures absolutely critical—no business, big or small, can afford to be complacent in the face of evolving threats.
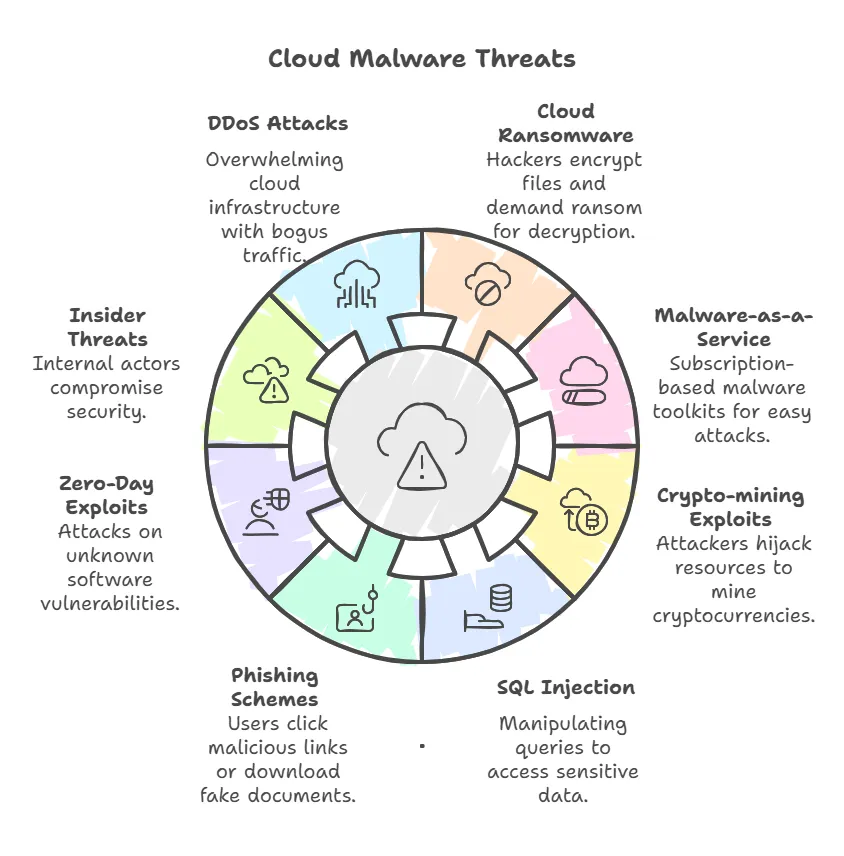
10 Most Dangerous Cloud Malware Attacks – A Must-Know List
Cybercriminals discover a goldmine of opportunities as organizations increasingly shift to the cloud for flexibility, cost savings, and scalability. Many of these threats, from cloud ransomware attacks to zero-day exploits, target your valuable data or hijack resources—potentially causing irreparable harm. Below are ten of the most insidious types of cloud malware, including what to watch out for and how to defend against each. By understanding these threats, you can better protect your business from avoidable security disasters.
1. Cloud Ransomware Attacks
When we talk about cloud ransomware attacks, hackers infiltrate your storage or applications hosted in the cloud, encrypt vital files, and demand ransom for decryption. Ransomware continues to be among the most profitable cyberattacks, often exploiting weak credentials or unpatched software. Quick mitigation steps include:
- Implementing offline backups
- Restricting admin privileges
- Running regular vulnerability assessments
By practicing these safeguards, you reduce the appeal of your cloud systems as a ransomware target.
2. Malware-as-a-Service
Among the most alarming cloud malware examples is Malware-as-a-Service (MaaS). Criminal developers offer subscription-based malware toolkits on the dark web, making it dangerously simple for even non-technical criminals to launch attacks. MaaS platforms often integrate with cloud hosting providers for global reach and efficient scaling. To counter:
- Use advanced malware detection tools
- Deploy behavioral analytics
- Monitor suspicious outbound traffic
Proactive scanning and employee awareness can minimize your exposure to MaaS.
Protect Your Cloud, Protect Your Business with Proactive Defenses
Work With Us3. Crypto-mining Exploits
Among the types of cloud malware, crypto-mining stands out for its stealth. Attackers hijack your CPU or GPU resources to mine cryptocurrencies, driving up costs and degrading performance. Norton notes that crypto-miners often go undetected for months. Look out for unexplained spikes in:
- CPU usage
- Electricity bills
- Server downtime
You can quickly detect abnormal activity and shut down crypto-miners by establishing usage baselines and setting up automatic alerts.
4. SQL Injection
SQL injection is a classic hack that becomes even more devastating when targeting cloud vulnerabilities. Attackers manipulate query inputs to access or delete sensitive data stored in cloud databases. OWASP ranks SQL injection as one of the most critical security risks. Protect your data by:
- Validating all user inputs
- Using parameterized queries
- Employing Web Application Firewalls (WAF)
Addressing these weaknesses early helps prevent large-scale data compromises.
5. Phishing Schemes
Phishing remains one of the most effective cloud attack vectors because users often unwittingly click malicious links or download fake documents. The FBI reports consistent year-over-year increases in phishing incidents. Key protective measures include:
- Email filtering and link scanning
- Routine security training for employees
- Multi-factor authentication (MFA)
It only takes one click to compromise your cloud environment, so vigilance is crucial.
6. Zero-Day Exploits
Zero-day exploits rank high among the top cloud threats because cybercriminals pounce on software vulnerabilities that even the vendor doesn’t yet know about. We advise frequent patching and robust threat intelligence to mitigate these unpredictable risks. Strengthen your defenses by:
- Maintaining a rapid patch management strategy
- Conducting frequent penetration testing
- Monitoring threat feeds for emerging exploits
The quicker you respond, the lower your exposure to undisclosed vulnerabilities.
7. Insider Threats
Your staff, contractors, or vendors might accidentally—or intentionally—open the door to a cybercriminal. Insider threats often bypass even the strongest external defenses. Practical steps to deter insider threats include:
- Enforcing least-privilege access
- Regularly reviewing employee permissions
- Using behavior analytics to spot unusual activity
Trust is important, but verification is essential.
| For More Cloud Computing Insights, Read Our Blog What is a Cloud Database: Definition, Benefits, Disadvantages & Types Why is Cloud Computing Important? The 5 Steps to a Successful Cloud Migration Strategy |
8. Denial of Service or DDoS
Denial of Service (DoS) or Distributed Denial of Service (DDoS) attacks overwhelm your cloud infrastructure with bogus traffic until legitimate requests can’t get through. Cloudflare notes that these attacks can peak at hundreds of gigabits per second. Protective steps include:
- Load balancing across multiple servers
- Using DDoS protection services
- Monitoring traffic for sudden spikes
Blocking malicious traffic early ensures your services remain accessible.
9. Supply Chain Attacks
Your cloud defense is only as strong as the weakest vendor in your supply chain. Attackers might compromise a third-party provider, granting them a hidden path into your environment. NIST recommends rigorous supply chain risk management, such as:
- Vetting vendors’ security postures
- Conducting periodic audits
- Restricting vendor access to necessary scope only
Stay selective about who can tap into your cloud resources.
10. Remote Desktop Protocol Exploits
A poorly configured RDP port can be like leaving your front door wide open. Cybercriminals can brute-force login credentials or exploit vulnerabilities to gain root access. We advise:
- Changing default RDP ports
- Using network-level authentication
- Deploying multi-factor authentication
Never underestimate how quickly an open port can be discovered and exploited.
How to Stay Safe in the Cloud
Given the rising intensity of attacks, staying secure in a cloud environment requires consistent vigilance. Here are some effective steps:
- Use Strong Access Controls:
Implement multi-factor authentication (MFA) to ensure only authorized personnel log in. Limit admin privileges to essential team members. - Encrypt All Data in Transit and at Rest:
Encryption acts as a protective layer, thwarting eavesdroppers and unauthorized access to sensitive information. - Update and Patch Frequently:
Keep cloud software, operating systems, and applications up to date. This reduces the risk of hackers exploiting known vulnerabilities. - Monitor Activity 24/7:
80% of organizations report that security awareness training has significantly reduced phishing susceptibility. Employ advanced monitoring solutions to detect unusual spikes in CPU usage or suspicious login attempts. Alerts should automatically trigger when anomalies arise. - Train Your Workforce:
Human error is one of the biggest security vulnerabilities. Regularly educate employees about phishing scams, safe password practices, and reporting suspicious activities. - Perform Regular Audits and Penetration Tests:
Schedule internal and external assessments to identify vulnerabilities before attackers do. This proactive approach helps you fix weaknesses early. - Back Up Data Offline:
Maintain secure, offline backups of all critical data. Should ransomware encrypt your files, you can restore operations without paying a ransom.
For more expert safety recommendations, check out CISA’s Cloud Security Tips.
By combining these best practices with a solid incident response plan, you can significantly reduce the risk of cloud-based attacks.
Quick Reference for 10 Cloud Malware Attacks
| Attack Type | Primary Risk | Best Defense Measures |
| Cloud Ransomware | Data encryption & extortion | Offline backups, privilege restrictions |
| Malware-as-a-Service (MaaS) | Ready-to-use hacking toolkits | Advanced malware detection, traffic monitoring |
| Crypto-mining Exploits | Resource hijacking | Usage baselines, auto alerts, robust patching |
| SQL Injection | Data theft or corruption | Input validation, parameterized queries, WAF |
| Phishing Schemes | Credential theft | Email filtering, security training, MFA |
| Zero-Day Exploits | Unpatched vulnerabilities | Rapid patching, threat intelligence, pen testing |
| Insider Threats | Unauthorized internal access | Least privilege, permission reviews, behavior analytics |
| Denial of Service (DoS/DDoS) | Service unavailability | DDoS protection, load balancing, traffic monitoring |
| Supply Chain Attacks | Compromised vendor infiltration | Vendor vetting, restricted access, audits |
| RDP Exploits | Direct unauthorized access | Change default ports, network-level auth, MFA |
Take Charge of Your Cloud Security with Computers Made Easy
The evolving nature of cloud malware means your business can’t afford to be reactive. From ransomware and phishing attacks to insider threats and zero-day vulnerabilities, each risk has the potential to cripple operations, expose sensitive data, or disrupt customer trust. But with the right protection strategies—strong access controls, encryption, regular audits, and continuous monitoring—you can create a resilient security posture.
Computers Made Easy is your dedicated partner in cybersecurity, providing proactive defenses and expert-managed services tailored to small and mid-sized businesses. Don’t wait for an attack to disrupt your business. Contact us today to schedule a personalized consultation and start protecting your cloud environment before it’s too late.
| Ask Our IT Consultants How You Can Streamline Your Cloud Security | |
| Portland, Oregon | Vancouver, Washington |



